« Designate with PowerDNS » : différence entre les versions
mAucun résumé des modifications |
Aucun résumé des modifications |
||
| Ligne 173 : | Ligne 173 : | ||
* List ''Designate'' zones : | * List ''Designate'' zones : | ||
<syntaxhighlight lang="bash"> | |||
$ openstack zone list | $ openstack zone list | ||
+--------------------------------------+-------------------+---------+------------+--------+--------+ | +--------------------------------------+-------------------+---------+------------+--------+--------+ | ||
Version du 16 octobre 2024 à 14:36
Configure Designate with a Powerdns backend.
The objective is to configure and deploy a DNS as a service.
The stack
Designate deploys its own DNS servers (designate-mdns) which will act as primary on its own managed zones.
These DNS servers are not intended to face client traffic. One or more PowerDNS servers (not deployed by Designate), configured as secondary for the zones managed by Designate, will act as the actual DNS root.
Designate will create its managed zones as secondaries in PowerDNS via the PowerDNS API. Subsequent updates (addition/deletion of records) will be managed via AXFR notifications.
It's possible (and recommanded) to put a recursor in front of this DNS root and why not a DNS load balancer such as dnsdist.
PowerDNS configuration
A complete guide to configure a PowerDNS stack is out of scope.
There are important settings to put in PowerDNS pdns.conf :
- webserver=yes
- webserver-port=<PORT>
- webserver-allow-from=<openstack_controller1_ip>,<openstack_controller2_ip>,<openstack_controller3_ip>
- api=yes
- api-key=<KEY>
- secondary=yes
- trusted-notification-proxy=<kolla_external_vip_address>
- allow-notify-from=<openstack_controller1_ip>,<openstack_controller2_ip>,<openstack_controller3_ip>
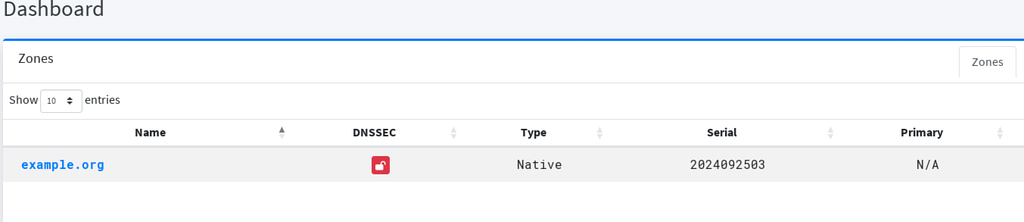
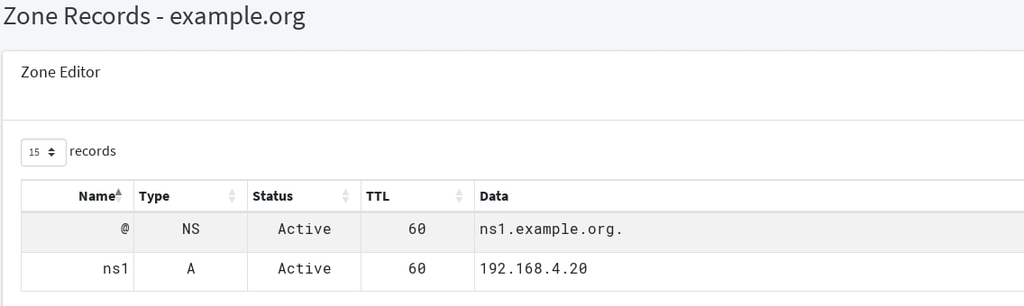
In this howto, PowerDNS is authoritative on example.org (PowerDNS-ADMIN screenshots) :
Kolla-ansible configuration and deployment
Patch to manage PowerDNS backends
Kolla-ansible manages only Bind or Infoblox backends by default.
A small patch is required to manage PowerDNS backends :
--- ./ansible/roles/designate/templates/pools.yaml.j2.orig 2024-09-25 10:56:16.610311548 +0200
+++ ./ansible/roles/designate/templates/pools.yaml.j2 2024-09-25 15:32:20.241690207 +0200
@@ -97,4 +97,38 @@
password: {{ designate_infoblox_auth_password }}
multi_tenant: {{ designate_infoblox_multi_tenant }}
ns_group: {{ designate_infoblox_ns_group }}
+{% elif designate_backend == 'pdns4' %}
+- name: pdns
+ id: {{ designate_pool_id }}
+ description: Default PowerDNS4 Pool
+ attributes: {}
+ ns_records:
+{% if designate_ns_record is string %}
+ - hostname: {{ designate_ns_record }}.
+ priority: 1
+{% else %}
+{% for host in designate_ns_record %}
+ - hostname: {{ host }}.
+ priority: 1
+{% endfor %}
+{% endif %}
+ nameservers:
+ - host: {{ designate_backend_pdns4_master }}
+ port: {{ designate_bind_port }}
+ also_notifies:
+ - host: {{ designate_backend_pdns4_master }}
+ port: {{ designate_bind_port }}
+ targets:
+ - type: pdns4
+ description: Default PowerDNS4 Pool
+ masters:
+{% for mdns_host in groups['designate-mdns'] %}
+ - host: {{ 'dns' | kolla_address(mdns_host) }}
+ port: {{ designate_mdns_port }}
+{% endfor %}
+ options:
+ host: {{ designate_backend_pdns4_master }}
+ port: 53
+ api_endpoint: http://{{ designate_backend_pdns4_master }}
+ api_token: {{ designate_backend_pdns4_token }}
{% endif %}
Configuration
Here is a globals.yml example settings for designate :
enable_designate: "yes"
designate_ns_record:
- "ns1.example.org"
designate_backend: "pdns4"
designate_backend_pdns4_master: "192.168.4.20:<PORT>"
designate_backend_pdns4_token: "<KEY>"
Deployment
With kolla-ansible configured, this is done with :
$ kolla-ansible deploy -i multinode --tags designate,neutron
Test !
Zone creation
- Let's create a acme.example.org. zone (the final dot is important !) :
$ openstack zone create --email admin@example.org acme.example.org.
...
$ openstack zone list
+--------------------------------------+-------------------+---------+------------+--------+--------+
| id | name | type | serial | status | action |
+--------------------------------------+-------------------+---------+------------+--------+--------+
| 2e38a414-effd-4409-9d12-e95dc34adc0c | acme.example.org. | PRIMARY | 1729087697 | ACTIVE | NONE |
+--------------------------------------+-------------------+---------+------------+--------+--------+
- Monitor PowerDNS activity :
Oct 16 14:08:18 AXFR-in zone: 'acme.example.org', primary: '10.30.0.3', zone committed with serial 1729087697
- See the result in PowerDNS-ADMIN :
- Test with dig :
$ dig @192.168.4.20 -t SOA acme.example.org. +short
ns1.example.org. admin.example.org. 1729087697 3572 600 86400 3600
$ dig @192.168.4.20 -t NS acme.example.org. +short
ns1.example.org.
Integration with Neutron
- Create a network and a subnet (remember, the final dot is important for --dns-domain !) :
$ openstack network create --dns-domain acme.example.org. acme-net
$ openstack subnet create --dns-publish-fixed-ip --subnet-range 172.16.20.0/24 --network acme-net --dhcp --gateway 172.16.20.1 acme-subnet
- Create a server
$ openstack server create --image cirros --flavor e1 --network acme-net vm1
$ openstack server list --format json | jq -r '.[] | select(."Name" == "vm1") | .ID'
914ac996-66cc-440b-a3ea-c7c785f5f080
$ openstack port list --device-id 914ac996-66cc-440b-a3ea-c7c785f5f080 -c ID -f value
80c07a07-3eed-4b38-aa1b-b433bef029a5
$ openstack port show 80c07a07-3eed-4b38-aa1b-b433bef029a5 -f value -c dns_assignment
[{'ip_address': '172.16.20.47', 'hostname': 'vm1', 'fqdn': 'vm1.acme.example.org.'}]
- Monitor PowerDNS activity (notice the in-addr.arpa zone activity):
Oct 16 14:22:10 AXFR-in zone: 'acme.example.org', primary: '10.30.0.14', zone committed with serial 1729088530
Oct 16 14:22:10 AXFR-in zone: '20.16.172.in-addr.arpa', primary: '10.30.0.3', zone committed with serial 1729088529
Oct 16 14:22:14 AXFR-in zone: '20.16.172.in-addr.arpa', primary: '10.30.0.3', zone committed with serial 1729088533
- Test with dig :
$ dig @192.168.4.20 -t A vm1.acme.example.org. +short
172.16.20.47
$ dig @192.168.4.20 -t PTR 47.20.16.172.in-addr.arpa. +short
vm1.acme.example.org.
- List Designate zones :
$ openstack zone list
+--------------------------------------+-------------------+---------+------------+--------+--------+
| id | name | type | serial | status | action |
+--------------------------------------+-------------------+---------+------------+--------+--------+
| 2e38a414-effd-4409-9d12-e95dc34adc0c | acme.example.org. | PRIMARY | 1729088530 | ACTIVE | NONE |
+--------------------------------------+-------------------+---------+------------+--------+--------+
# Only admins can list "in-addr.arpa" zones
$ openstack zone list --all-projects
+--------------------------------------+----------------------------------+-------------------------+---------+------------+--------+--------+
| id | project_id | name | type | serial | status | action |
+--------------------------------------+----------------------------------+-------------------------+---------+------------+--------+--------+
| 2e38a414-effd-4409-9d12-e95dc34adc0c | 32dd19f16d474c0fad025b89139b935a | acme.example.org. | PRIMARY | 1729088530 | ACTIVE | NONE |
| 84fe8412-2dc9-43a3-aa46-d6774309bd03 | 385b4f15b3974f45a4a55b06f8f0ab39 | 20.16.172.in-addr.arpa. | PRIMARY | 1729088533 | ACTIVE | NONE |
+--------------------------------------+----------------------------------+-------------------------+---------+------------+--------+--------+