« Keystone with OpenID Connect » : différence entre les versions
Sauter à la navigation
Sauter à la recherche
(Page créée avec « Configure an external [https://www.keycloak.org/ Keycloak] to provide authentication for [https://docs.openstack.org/keystone/latest/ Keystone] == Keycloak client configuration == This guide assumes you already have a working Keycloak server. <br /> What is covered here is how to : * create a client in Keycloak for Keystone * configure this client ») |
Aucun résumé des modifications |
||
| Ligne 1 : | Ligne 1 : | ||
Configure an external [https://www.keycloak.org/ Keycloak] to provide authentication for [https://docs.openstack.org/keystone/latest/ Keystone] | Configure an external [https://www.keycloak.org/ Keycloak] to provide authentication for [https://docs.openstack.org/keystone/latest/ Keystone] | ||
<br /> | |||
The objective is to identify a user and allow them to find their projects in Openstack. | |||
== Keycloak client configuration == | == Keycloak client configuration == | ||
| Ligne 8 : | Ligne 11 : | ||
* create a client in Keycloak for Keystone | * create a client in Keycloak for Keystone | ||
* configure this client | * configure this client | ||
=== Client creation and settings === | |||
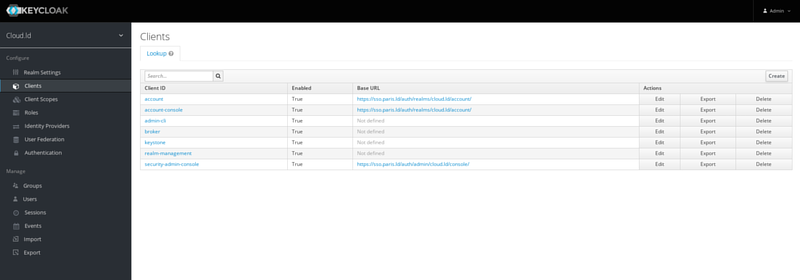
* Got to your Keycloak admin console and configure a new client (click ''Create'') | |||
[[Fichier:keycloak1.png|800px|thumb|center|Keycloak admin console]] | |||
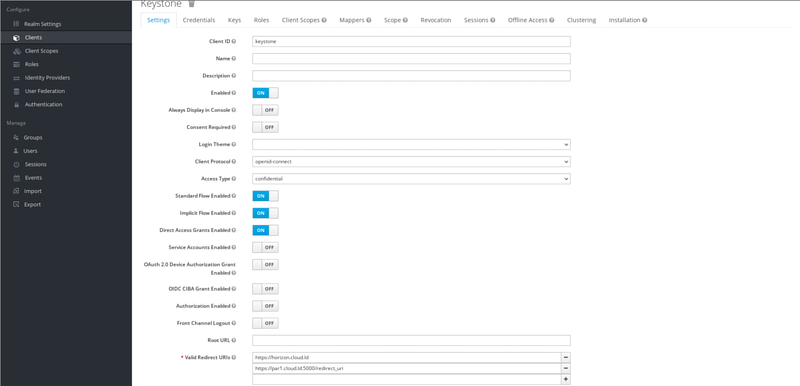
* Let's assume your client is named ''Keystone'' | |||
** Leave ''Root URL'' empty | |||
** Select ''openid-connect'' for ''Client Protocol'' | |||
** Select ''confidential'' for ''Access Type'' | |||
** ''Standard Flow Enabled'', ''Implicit Flow Enabled'' and ''Direct Access Grants Enabled'' must be on | |||
** The *fqdn* for ''Valid Redirect URIs'' should match the value of ''kolla_external_fqdn''. If your ''kolla_internal_fqdn'' is ''par1.cloud.ld'', then your ''Valid Redirect URIs'' should be ''https://par1.cloud.ld:5000/redirect_uri''. You can also add the URI of your [https://docs.openstack.org/horizon/latest/ Horizon dashboard] | |||
[[Fichier:keycloak2.png|800px|thumb|center|Keycloak client settings]] | |||
* Don't forget to copy the client's key (via ''Credentials'' tab) | |||
=== Client mappers === | |||
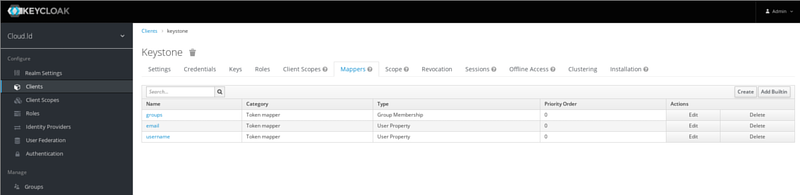
Add the following mappers to the new client : | |||
* ''groups'' via ''Add Builtin'' button and type ''Group Membership'' | |||
* ''email'' via ''Add Builtin'' button and type ''User Property'' | |||
* ''username'' via ''Add Builtin'' button and type ''User Property'' | |||
[[Fichier:keycloak3.png|800px|thumb|center|Keycloak client mappers]] | |||
Version du 21 février 2024 à 15:26
Configure an external Keycloak to provide authentication for Keystone
The objective is to identify a user and allow them to find their projects in Openstack.
Keycloak client configuration
This guide assumes you already have a working Keycloak server.
What is covered here is how to :
- create a client in Keycloak for Keystone
- configure this client
Client creation and settings
- Got to your Keycloak admin console and configure a new client (click Create)
- Let's assume your client is named Keystone
- Leave Root URL empty
- Select openid-connect for Client Protocol
- Select confidential for Access Type
- Standard Flow Enabled, Implicit Flow Enabled and Direct Access Grants Enabled must be on
- The *fqdn* for Valid Redirect URIs should match the value of kolla_external_fqdn. If your kolla_internal_fqdn is par1.cloud.ld, then your Valid Redirect URIs should be https://par1.cloud.ld:5000/redirect_uri. You can also add the URI of your Horizon dashboard
- Don't forget to copy the client's key (via Credentials tab)
Client mappers
Add the following mappers to the new client :
- groups via Add Builtin button and type Group Membership
- email via Add Builtin button and type User Property
- username via Add Builtin button and type User Property